Since, like anyone else, I receive tons of scam emails and snail mail letters, I decided to present here some of these. All of these (and many more which I just delete) are scams. This means, what the senders have in mind is to racket one of us. And according to what I've seen, they do succeed quite often.
If you have similar letters in your mailbox, either disregard or play with the person knowing that you can't give him (or her) any information about:
-
Your bank account,
-
Your address — or any valid address if that matter,
-
Your family, and
-
any other information that you judge private or even intimate.
Ha! I say "Your"... even if you don't like your neighbor at all, don't give his information either. The Internet leaves tracks (hackers in the US are being caught one after another!) and you would certainly be in even bigger trouble.
In the meantime, I hope you will enjoy reading these letters as I do myself once in a while. 8-)I do not always add comments with the letters since I usually don't have time to do so, but there would often be a lot of joke to tell!

|
Latest Scams |
-
Last update: 11/23/2014
X-Apparently-To: alexis_wilke@yahoo.com via 206.190.38.195; Fri, 08 Apr 2005 05:55:35 -0700
Authentication-Results: mta251.mail.scd.yahoo.com from=virgilio.it; domainkeys=neutral (no sig)
X-Originating-IP: [212.216.176.118]
Return-Path: <v_atlantic@virgilio.it>
Received: from 212.216.176.118 (EHLO vsmtp14.tin.it) (212.216.176.118)
by mta251.mail.scd.yahoo.com with SMTP; Fri, 08 Apr 2005 05:55:35 -0700
Received: from ims1d.cp.tin.it (192.168.70.101) by vsmtp14.tin.it (7.0.027) id 4227B87800E7F5EB
for alexis_wilke@yahoo.com; Fri, 8 Apr 2005 14:55:33 +0200
Received: from ...
-
Last update: 11/23/2014
For this one I don't have the email header, but it's still a funny one! The first image is what I received and it's totally unreadable. I don't even see why anyone would want to try to decipher it! The 2nd image is what you can get once you applied some very simple transformations to the source. In other words, the scrambling there is totally useless.
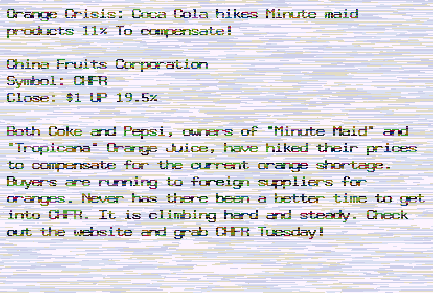

-
Last update: 07/06/2017
The link in the email was sending you to http://www.e-gold.prixeco.com/. So not e-gold, but prixeco instead!
Return-Path: <SecurityRobot_donotreply@e-gold.com>
X-Original-To: alexis@halk.m2osw.com
Delivered-To: alexis@halk.m2osw.com
Received: from mail.m2osw.com (jcolo [69.55.238.181])
by halk.m2osw.com (Postfix) with ESMTP id 7A48E1BF31
for <alexis@halk.m2osw.com>; Thu, 12 Jun 2008 08:58:09 -0700 (PDT)
X-Greylist: delayed 3448 seconds by postgrey-1.27 at web.m2osw.com; Thu, 12 Jun 2008 08:58:07 PDT
Received: from flpi185.prodigy.net (flpi185.sbcis.sbc.com ...
-
Last update: 11/23/2014
I thought I'd put this one because it looks pretty good. That is, it really looks like the bank talking to you. Thought a bank is very unlikely going to send you an email which is just one single image and of course event less an email which asks you for all your personal information since they already have them.
Since this is an image, it is easy for it to show a correct URL. Of course, it would send you to another server, not the bank's.
Of course, since I live in California and the bank does not opperate here, I don't have an account with them anyway...
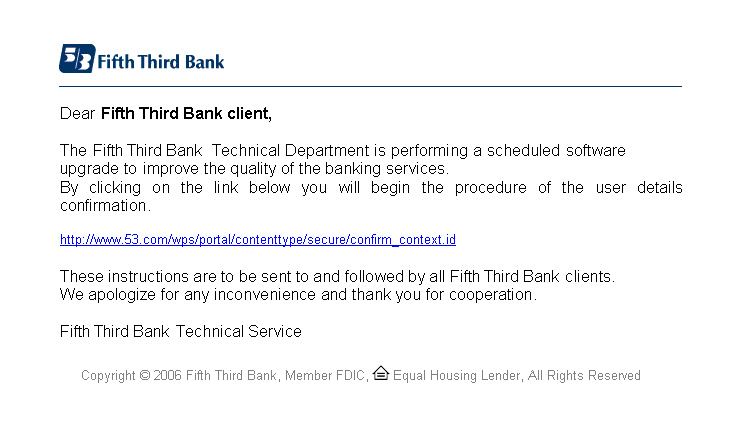
Note: I added the ...
-
Last update: 10/31/2009
I suppose I'd have to pay him loads of money for -450Kg of gold...
(yes, see the minus sign?!, I know, it's part of the :- and not
really the number, but, sorry, it just looks too silly here.)
-
Last update: 11/23/2014
This is going on and on with pretty much all the banks I ever heard of. Many with British banks now and my less global banks! It looks like the phishers are targeting smaller banks which certainly have much less money to spend on protecting their users from giving away their credentials. This scheme most certainly work. According to the numbers I have seen, 1 in 100 people will fall for it and these people lose US $800 on average. This is quite expensive!
Notice that this one is using an account of some sort at the University of Toronto for the fake page. The URL is really bad! But still, ...
-
Last update: 11/23/2014
Quite interesting email. First the header includes some broken entries with the missing space after the : (i.e. X-EYOU-SPAMVALUE) Then the email itself sounds like the bank can only secure its login stuff with your help. I guess they could not just turn off your account and voila...
Return-Path: <security@regions.com>
X-Original-To: alexis@halk.m2osw.com
Delivered-To: alexis@halk.m2osw.com
Received: from mail.m2osw.com (jcolo [69.55.238.181])
by halk.m2osw.com (Postfix) with ESMTP id 132B31BDE4
for <alexis@halk.m2osw.com>; Thu, 14 Feb 2008 15:45:07 -0800 ...
-
Last update: 10/31/2009
You've got to love them! Read the 1st paragraph. Way cool! He's
not a bad guy at all...
-
Last update: 11/24/2014
This one is yet another about tons of money I just win by magic! Someone just happened to get my email addres, and actually, this email was not even sent to me (look at the To: ... I was on the Bcc:, any reason you can think of?)
What I laught about is the number of times I received it in my mailbox. There is a picture:
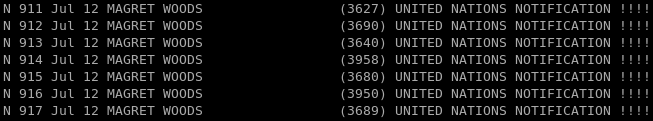
And before I posted this image on this website I received yet another email from MAGRET WOODS!
Ha! Ha! Ha! That's too much! I could block these emails, obviously, but I did not and I got another 10 in the past 2 hours. So... Am I going to believe that stuff?!
...
-
Last update: 09/04/2009
Received: from snap.turnwatcher.com by substitute with [XMail 1.22 ESMTP Server]
id <S8BC5> for <@mail.m2osw.com:alexis@halk.m2osw.com>
from <kutangploy@adinet.com.uy>; Tue, 11 Jul 2006 11:54:40 -0700
Received: from smtp-s2.antel.net.uy (smtp-s2.antel.net.uy [200.40.30.223])
by snap.turnwatcher.com (Postfix) with ESMTP id 7D40726AD83
for <alexis@m2osw.com>; Tue, 11 Jul 2006 11:55:23 -0700 (PDT)
Received: from fe-ps01 (192.168.2.201) by smtp-s2.antel.net.uy (7.2.072.1)
(authenticated as kutangploy@adinet.com.uy)
id 447497B0010
|






